15 million + (Taiwan attacks) static signatures Next-gen AI unknown malicious threat program behavior analysis
30 million+ (Taiwan attacks) hacker IPs and short-term domains Sandbox malicious hyperlink download analysis
APT attack connection counter Sandbox malware behavior analysis
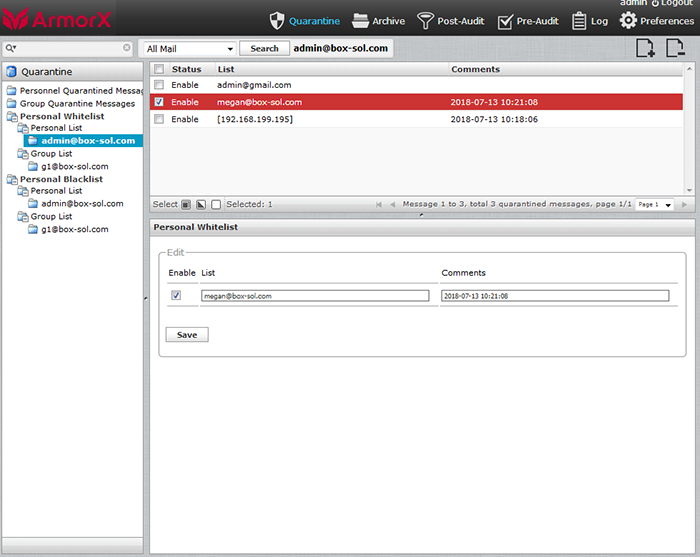
Double authentication whitelist
after locking on its target, collects intelligence, designs bait, and performs various tasks. Some common baits include impersonating customers, government agencies, and other well-known service providers, such as Apple, Google, the State Administration of Taxation, the Health Insurance Bureau, and international express delivery agencies.
Such socially engineered mail are not suspected as advertisements due to the content of the email, and the exploitation of traditional email gateway weaknesses to set the email address of the current unit as a system or personal whitelist, thereby removing any barriers against such fraudulent commercial email.
Our system has the world's most cutting-edge fraudulent email identification technology, providing an exclusive dual-verification whitelisting mechanism, meaning that the sender's mailbox plus the sender's host must both be approved before the mail can be released; and our exclusive SMTP delay counter, prohibit the hacker from utilizing system resources for replies, forcing the hacker to respond.
from the perspective of a programmer, customizes the simulation program,
recognizes and automatically classifies the language library, and defines the ratings of each type of project, including
Attachment type:
attachment encryption, forged subfile name, bomb compression (ZIP Bomb), decompression times
Characteristic database:
complete (Md5), multi-segment (Ssdeep), loading (Imphash) sampling, original database
Program behavior:
Antidebug Antivm, CVE Vulnerability, encryption calculus, Exploit Kits, Packers Hidden, Webshells , email identification, malicious files, malware, mobile malware, malicious URLs
Sandbox analysis (optional - independent dynamic sandbox simulation system):
behavior analysis, network analysis
| Purpose and Technique | Encryption extortion | Transaction Fraud | Control the system | Steal information and resources | Paralysis blackmail |
|---|---|---|---|---|---|
| Collect informtaion | ● | ● | ● | ● | ● |
| Designs bait | ● | ● | ● | ● | |
| Establishes relay station | ● | ● | |||
| CALL Home | ● | ● | |||
| Implants program | ● | ● | |||
| Executes mission | ● | ● | ● | ● | |
| Network integrated attack | ● |
Design Bait Its purpose is to identify an organizational weaknesses and send malicious hyperlinks or attachments;
CALL HomeTo obtain more malicious programs;
BEC Transaction Fraud The purpose behind the infiltration phase is to obtain the account and password of the user of the mail system. The purpose of the fraud phase is to obtain the remittance.
| Method | Interception Rate |
|---|---|
|
First-time malicious threat Communication behavior analysis First-time malicious threat Program behavior analysis |
85-95% |
|
Dynamic sandbox forensics Instant static signature |
10-30% |

Using the global exclusive patented technology "SMTP Instant Traceback" and "SMTP Hacker Behavior Analysis," you can effectively identify spam, illegal, anonymous, fraudulent, and other malicious mailing behaviors during the SMTP handshake phase.
Determined, decisive, and efficient blocking of more than 90% of spam; cloud reputation blacklist, international blacklist, DNSRBL, content weight calculation, etc., all come together to bring the best and most complete protection for enterprises.
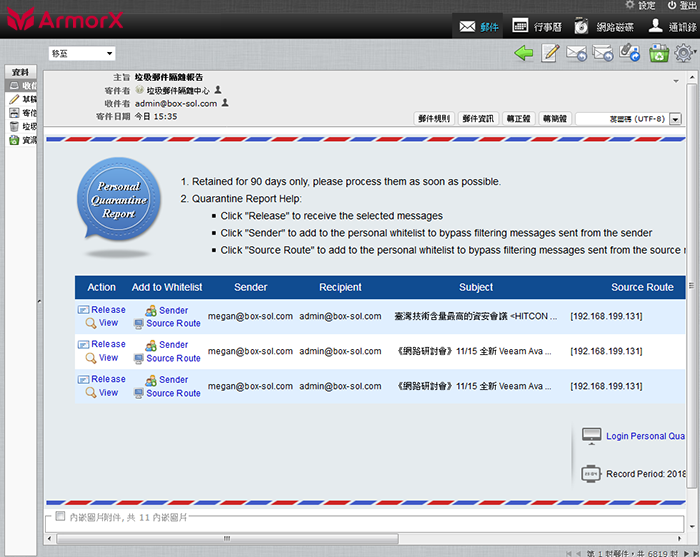
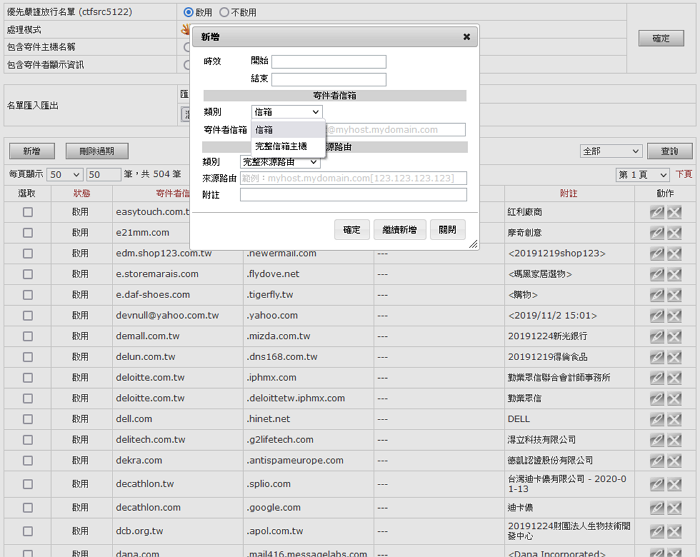
SpamTrap provides self-learning, policy comparison, blacklist reporting, whitelist feedback, personal and group policy development and black and white lists, overdue unread management, agents, quarantine reports, resend reports, aliases, group merges, and other pinpoint functions.
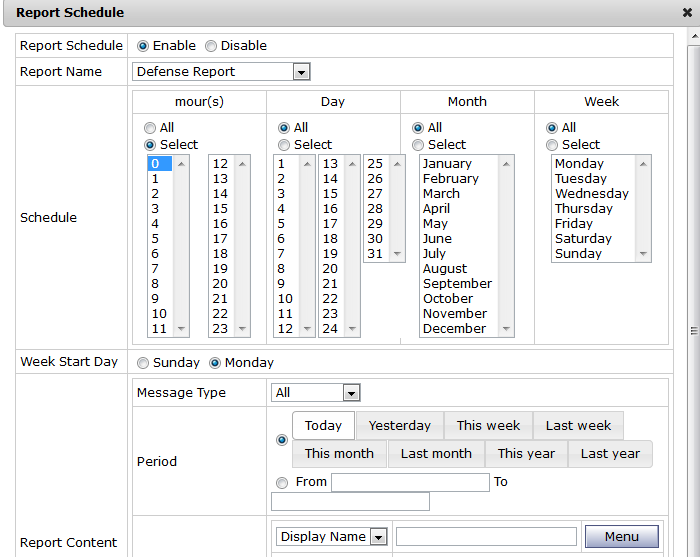
SpamTrap provides a variety of statistical charts and leaderboards, and can send statistics reports to department heads in a timely manner, according to the organizational structure.
The schedule can be immediately sent, or sent on a specified month, week, day, and time;
the content includes periods (starting with today, yesterday, this week, last week, this month, last month, this year, last year) and risk level;
regular input comparison of sender, recipient, subject, source routing, message code;
recipients can add their own, custom report format (supports webpage, text, PDF).